The True Story of How One Business Survived Two Cyber Attacks
Video Transcript
 What would happen to your business if all of your employees were suddenly unable to access any data and you saw a message like this [see image] appearing on your computers.
What would happen to your business if all of your employees were suddenly unable to access any data and you saw a message like this [see image] appearing on your computers.
What would you do?
In this video, I’m going to walk you through a short case study of one business that was hit with ransomware on two different occasions but at two very different outcomes. One being about three days’ worth of downtime and the other being only a couple of hours.
[Intro Music]
Hey everyone, this is Tyler with Innovative. Ransomware is an ugly reality, but one that businesses need to be prepared to deal with. In this video I’m going to walk you through a short case study of one business that was hit with ransomware on two different occasions but at two very different outcomes. One being about three days’ worth of downtime and the other being only a couple of hours.
As a managed service provider, we often have businesses come to us for guidance on how to deal with cyber threats such as ransomware. What I want to do is start with defining what ransomware is, and what you can about it.
Think of ransomware as a typical computer virus. The biggest difference is that instead of being malicious and deleting your data or even stealing your passwords the real purpose of this ransomware is to seek out what data that it can find as a first step. When you’re at home that might be just your computer, your personal computer and the data that’s on it. When you’re in a business setting you have access to a lot more shared data.
The second step in a typical ransomware attack is once it investigates what data that it can reach, it goes out and it begins encrypting it. What that really means to you is that you can no longer access this data. It makes it so that you cannot open it with any typical software applications and you can’t do anything about it once it has been encrypted.
The final phase of these attacks is a ransomware message that typically pops up on the infected machine and shows a ransom message indicating that you need to now pay this ransom in order to get access to the files again.
Paying the ransom is never an appropriate strategy in these situations. There have been many, many documented cases where even paying the ransom did not get data back for these businesses.
You might be asking yourself, “how can I prevent ransomware from happening in the first place?” It’s true there are multiple layers such as a firewall with intrusion prevention, content filtering, software-based firewalls, even added network security that can prevent things like this from occurring. In reality, the end user is typically how these infections start in the first place.
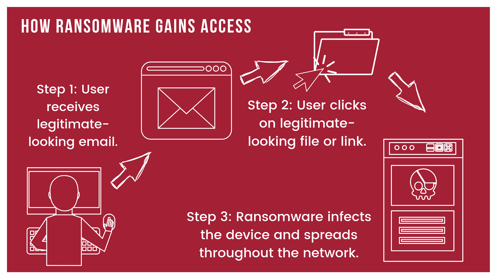 The best example, or the one that we typically see the most is a user clicking a link within an email that was not valid, it might look like it’s coming from Amazon or UPS, and once this machine is infected the damage has started and you often don’t know about it for quite some time.
The best example, or the one that we typically see the most is a user clicking a link within an email that was not valid, it might look like it’s coming from Amazon or UPS, and once this machine is infected the damage has started and you often don’t know about it for quite some time.
Truly, the only remediation strategy at this point is a good backup and recovery solution.
Let’s talk about our customer that was infected with ransomware.
It all started with a call coming in early one morning that just indicated that one user couldn’t get into a couple of files. As we were assessing this issue, pretty soon after, other users were calling in all reporting similar issues.
We quickly found out this was a bigger issue than we had anticipated, and our worst fears became realized when a ransomware message popped up on one of their machines.
The best strategy at this point is to make sure the infected machine is taken off the network, which is what we did. We want to make sure that is cleaned up or re-imaged sometimes to make sure that the infection is gone, but in this case the damage had been done and after we were done assessing the damage over one terabyte of the customer’s data was encrypted. They could not access it, and all of a sudden 80 users were down and they could not take care of their customers.
Fortunately, the customer did have a fully functional, cloud based, file backup system. It was protecting the data multiple times a day and retaining several weeks of data off site. We began going into a disaster mode and we began recovering this data back to their server.
It took over three full days until this customer was fully back up and running again. The backup worked as intended but it wasn’t aligned with the customer’s Recovery Time Objective or RTO. The customer wasn’t able to be down for days, they needed to be up and running in hours and the backup strategy wasn’t aligned.
We sat down with this customer once they were finally running again and helped them understand what an appropriate recovery time objective would be for their business. We helped them to understand how long they could be down and what it actually cost them to be down. We then took those variables and put them into an appropriate backup solution.
We ended up deploying an image-based, hybrid backup solution.
The image backup solution is very different from a file-based backup in that it protects the entire server and not just picking different files and folders.
The hybrid piece of this means that a local component was on site so that we could have the speed if a recovery was needed, but we also want to have the off-site functionality in case of a local disaster, or even something as simple as sprinklers going off would damage hardware. We wanted to make sure the business’s data was protected.
I wish I could tell you this was the end of their story, but unfortunately this customer was re-infected with ransomware several weeks later. It came in the same way as before where one user called in not being able to access files. We quickly remedied the situation and pulled the infected machine off of the network. This time, instead of deleting all the old data as we had before and beginning recovering from their file backup we had a new backup strategy in place.
We shut down the infected server. We took the most recent recovery point that was not infected from the backup device, and we booted up the server virtually on this appliance. This got the customer back up and running much quicker, and after some brief testing with a couple of key staff users we opened it up to everyone and all in all within one hour the customer was fully back up and running without any issues. No one had to be reconnected or re-pointed to anything, it was just as if the server healed itself and was back online again.
A few days later the customer gave me a call to say, “thank you.” He appreciated that our team was able to recover him so quickly. He appreciated that he had the right solution for his business and I’m very happy to report that this customer is thriving, and we are still their trusted IT advisers.
 I would strongly advise anyone watching this video to take a moment and sit down with their trusted IT advisers and discuss what their current backup solution is. Make sure the strategy aligns with your recovery time objective, so that you’re not caught in a similar situation like our customer was the first time.
I would strongly advise anyone watching this video to take a moment and sit down with their trusted IT advisers and discuss what their current backup solution is. Make sure the strategy aligns with your recovery time objective, so that you’re not caught in a similar situation like our customer was the first time.
We would be more than happy to sit down and discuss these same things with you if you don’t already have a trusted IT adviser.
Thank you guys so much, we really appreciate you watching this.
Have a fantastic day.
[Ending Music]
Want to Learn About Partnering with Innovative?
Schedule a call or contact us at 301.739.7414 to see if your business could benefit from a strategic technology partnership with Innovative.